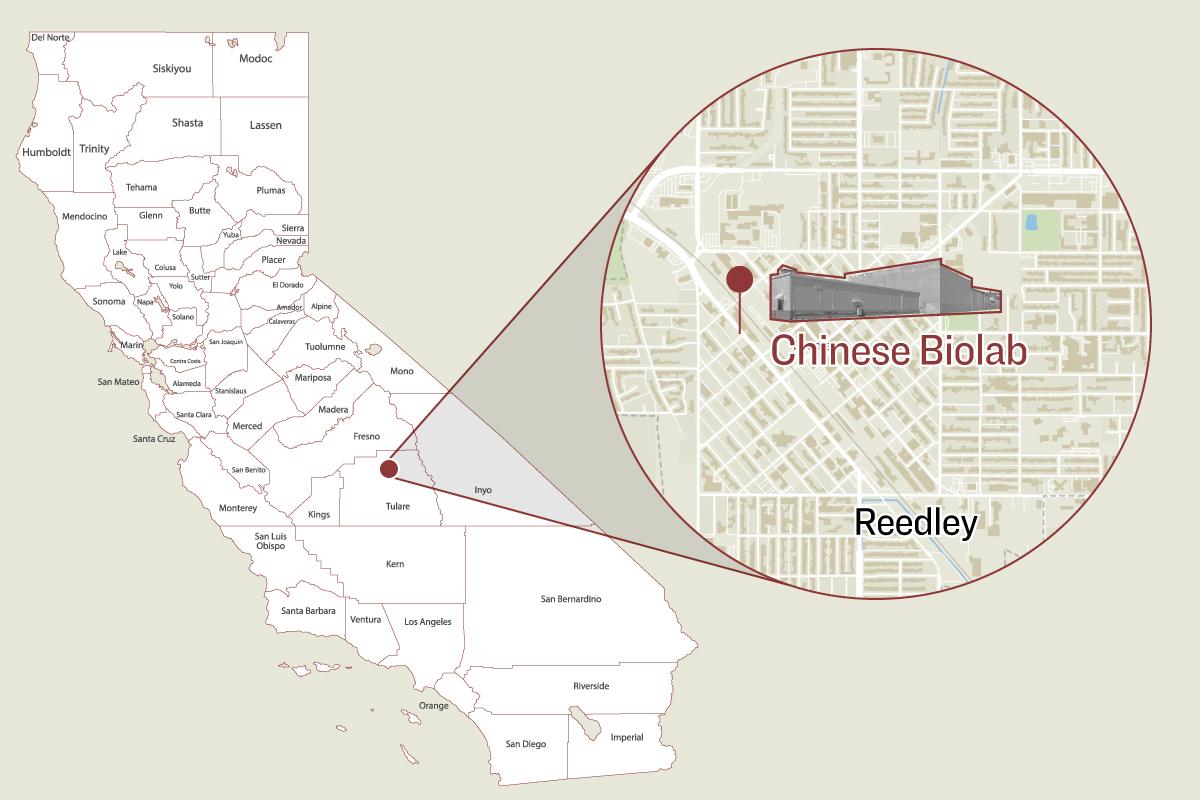
US officials search for hidden Chinese malware that could affect military operations
The administration believes malicious computer code has been hidden inside “networks controlling power grids, communications systems and water supplies that feed military bases,” officials told the Times. The discovery has heightened concerns that hackers could “disrupt US military operations in the event of a conflict,” according to the Times. The two nations have been increasingly at odds over Taiwan as well as over China’s actions in the Indo-Pacific.
One congressional official told the newspaper that the malware was “a ticking time bomb” that could allow China to cut off power, water and communications to military bases, slowing deployments and resupply operations. Because military bases often share the same supply infrastructure as civilian homes and businesses, many other Americans could also be affected, officials told the Times.
The malware revelations echo a pattern of recent breaches by China-based hackers previously reported by CNN.
The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies
The attack by Chinese spies reached almost 30 U.S. companies, including Amazon and Apple, by compromising America’s technology supply chain, according to extensive interviews with government and corporate sources.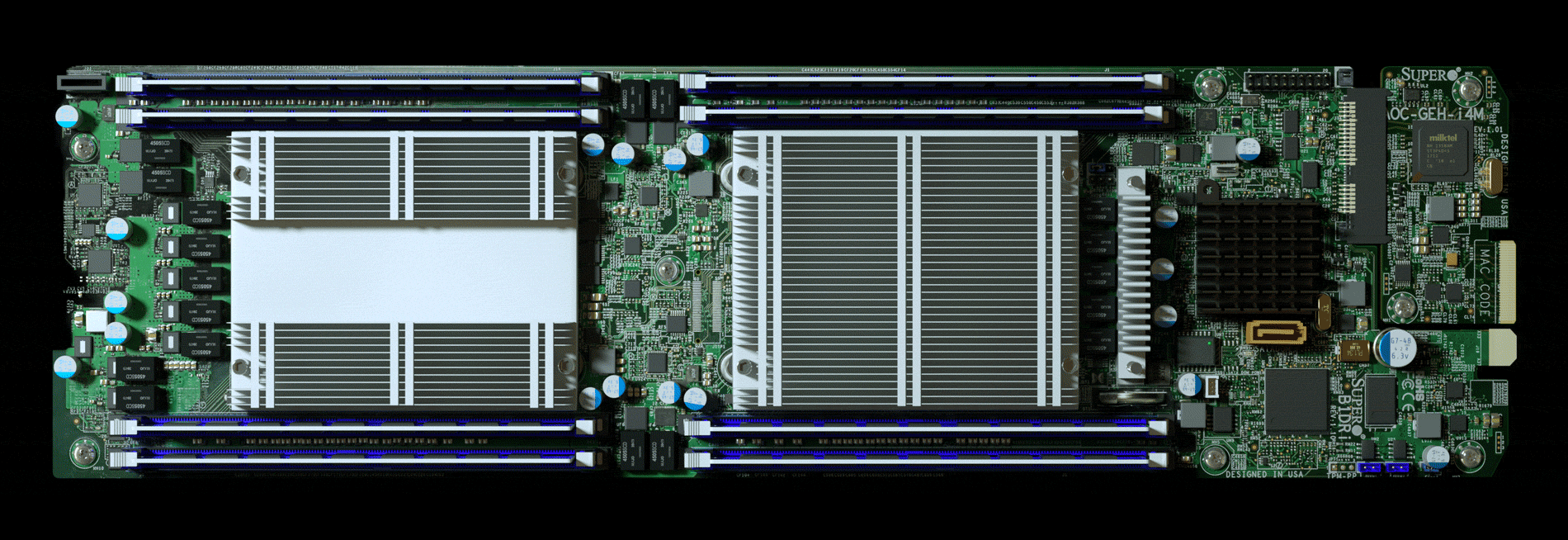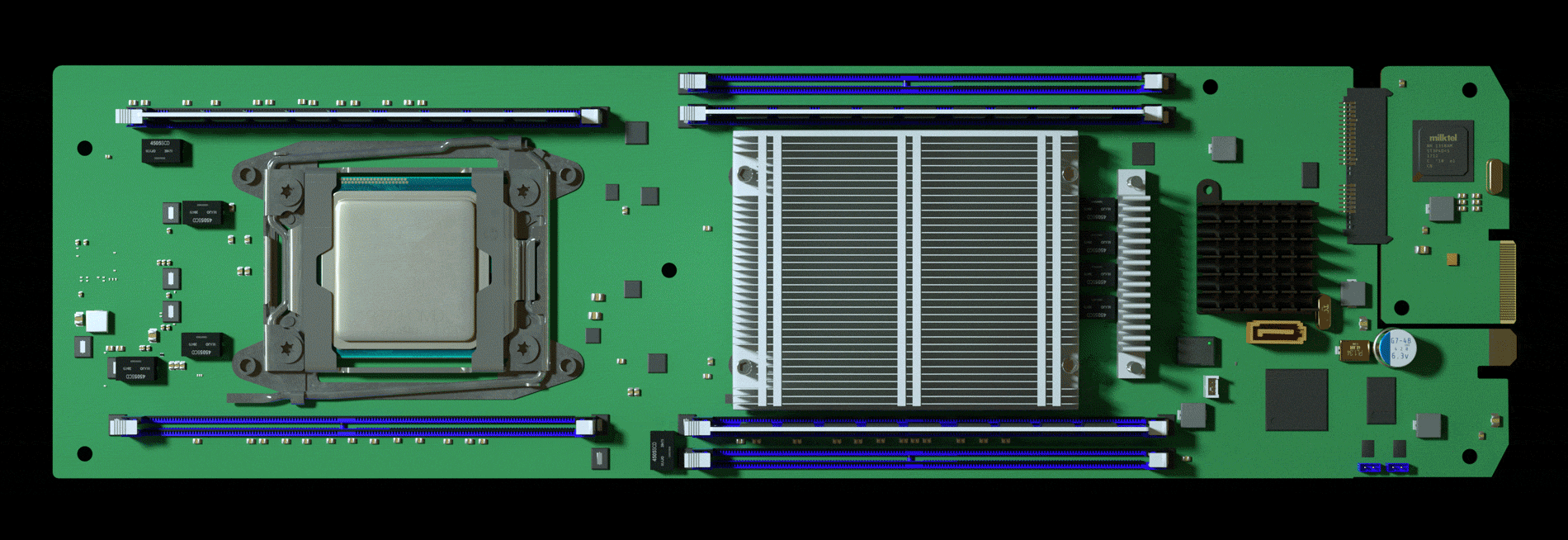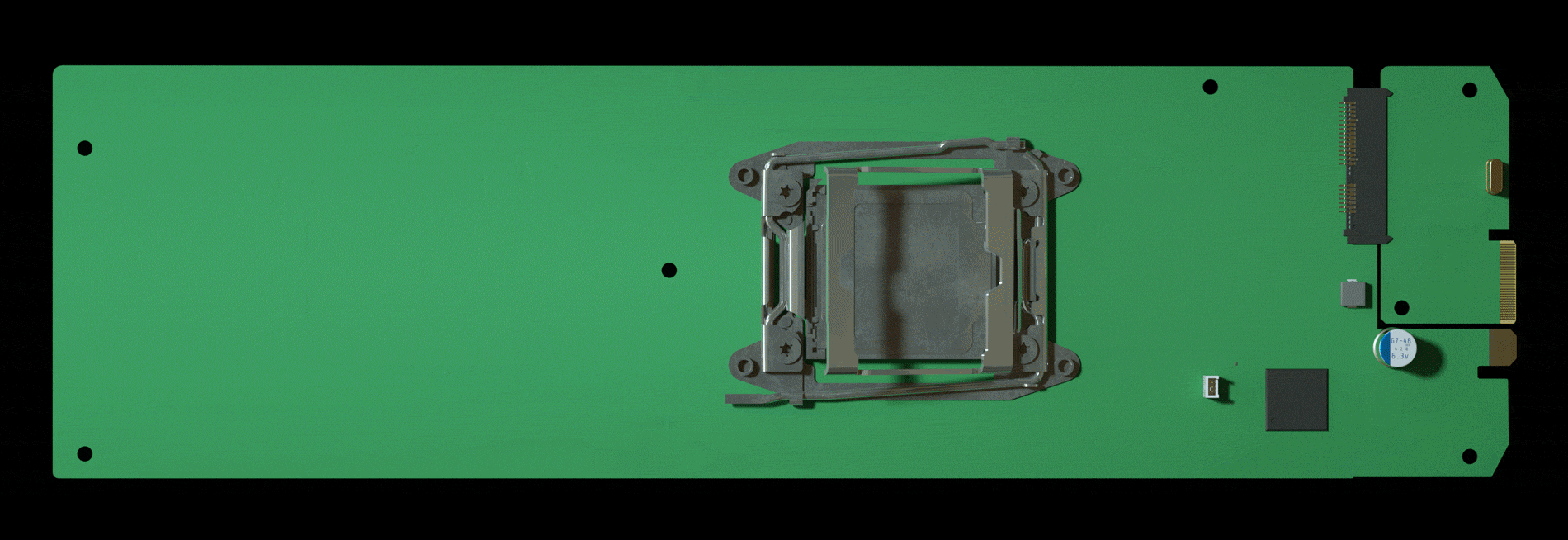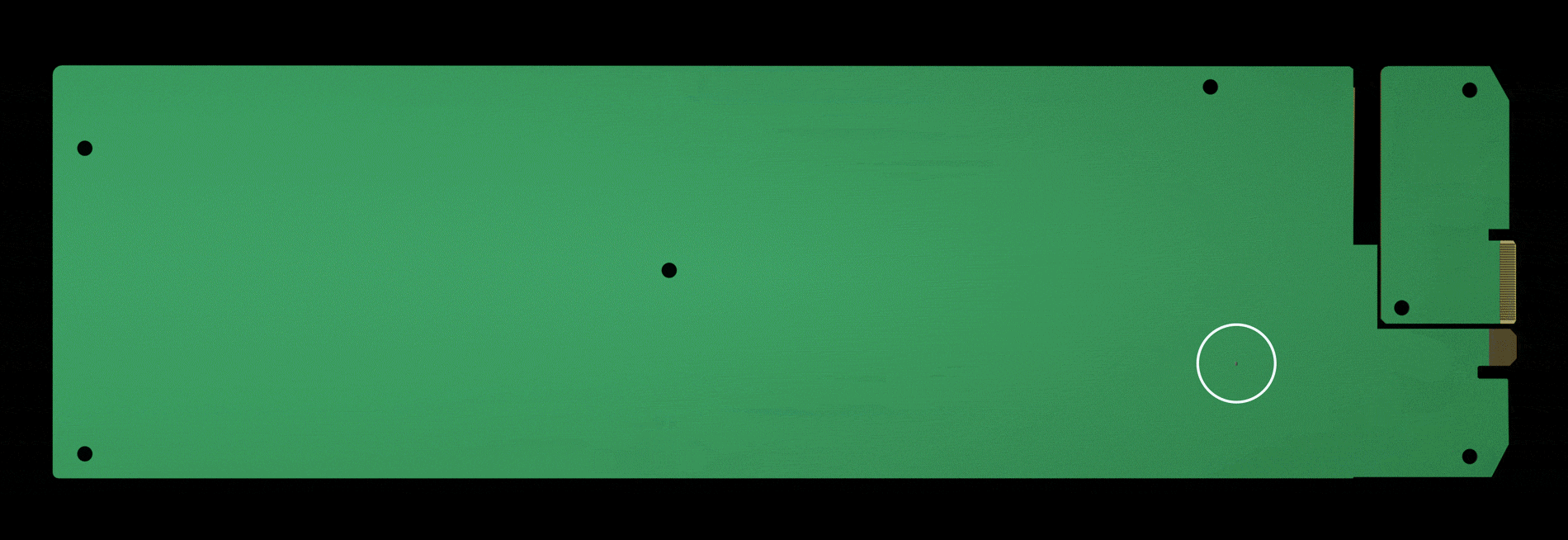
In 2015, Amazon.com Inc. began quietly evaluating a startup called Elemental Technologies, a potential acquisition to help with a major expansion of its streaming video service, known today as Amazon Prime Video. Based in Portland, Ore., Elemental made software for compressing massive video files and formatting them for different devices. Its technology had helped stream the Olympic Games online, communicate with the International Space Station, and funnel drone footage to the Central Intelligence Agency. Elemental’s national security contracts weren’t the main reason for the proposed acquisition, but they fit nicely with Amazon’s government businesses, such as the highly secure cloud that Amazon Web Services (AWS) was building for the CIA.
To help with due diligence, AWS, which was overseeing the prospective acquisition, hired a third-party company to scrutinize Elemental’s security, according to one person familiar with the process. The first pass uncovered troubling issues, prompting AWS to take a closer look at Elemental’s main product: the expensive servers that customers installed in their networks to handle the video compression. These servers were assembled for Elemental by Super Micro Computer Inc., a San Jose-based company (commonly known as Supermicro) that’s also one of the world’s biggest suppliers of server motherboards, the fiberglass-mounted clusters of chips and capacitors that act as the neurons of data centers large and small. In late spring of 2015, Elemental’s staff boxed up several servers and sent them to Ontario, Canada, for the third-party security company to test, the person says.
Nested on the servers’ motherboards, the testers found a tiny microchip, not much bigger than a grain of rice, that wasn’t part of the boards’ original design. Amazon reported the discovery to U.S. authorities, sending a shudder through the intelligence community. Elemental’s servers could be found in Department of Defense data centers, the CIA’s drone operations, and the onboard networks of Navy warships. And Elemental was just one of hundreds of Supermicro customers.
During the ensuing top-secret probe, which remains open more than three years later, investigators determined that the chips allowed the attackers to create a stealth doorway into any network that included the altered machines. Multiple people familiar with the matter say investigators found that the chips had been inserted at factories run by manufacturing subcontractors in China.
This attack was something graver than the software-based incidents the world has grown accustomed to seeing. Hardware hacks are more difficult to pull off and potentially more devastating, promising the kind of long-term, stealth access that spy agencies are willing to invest millions of dollars and many years to get.
The Long Hack: How China Exploited a U.S. Tech Supplier
Whether that probe continues is unknown, as is a full account of its findings. But as recently as 2018, the FBI enlisted private-sector help in analyzing Supermicro equipment that contained added chips, according to an adviser to two security firms that did the work.
The Supermicro saga demonstrates a widespread risk in global supply chains, said Jay Tabb, a former senior FBI official who agreed to speak generally about China’s interference with the company’s products.
“Supermicro is the perfect illustration of how susceptible American companies are to potential nefarious tampering of any products they choose to have manufactured in China,” said Tabb, who was the executive assistant director of the FBI’s national security branch from 2018 until he retired in January 2020. “It’s an example of the worst-case scenario if you don’t have complete supervision over where your devices are manufactured.”
China’s exploitation of products made by Supermicro, as the U.S. company is known, has been under federal scrutiny for much of the past decade, according to 14 former law enforcement and intelligence officials familiar with the matter. That included an FBI counterintelligence investigation that began around 2012, when agents started monitoring the communications of a small group of Supermicro workers, using warrants obtained under the Foreign Intelligence Surveillance Act, or FISA, according to five of the officials.
Whether that probe continues is unknown, as is a full account of its findings. But as recently as 2018, the FBI enlisted private-sector help in analyzing Supermicro equipment that contained added chips, according to an adviser to two security firms that did the work.
The Supermicro saga demonstrates a widespread risk in global supply chains, said Jay Tabb, a former senior FBI official who agreed to speak generally about China’s interference with the company’s products.
“Supermicro is the perfect illustration of how susceptible American companies are to potential nefarious tampering of any products they choose to have manufactured in China,” said Tabb, who was the executive assistant director of the FBI’s national security branch from 2018 until he retired in January 2020. “It’s an example of the worst-case scenario if you don’t have complete supervision over where your devices are manufactured.”
Supermicro spy chips, the sequel: It really, really happened, and with bad BIOS and more, insists Bloomberg
The article – a follow-on to BusinessWeek's 2018 spy chip bombshell – cites three specific incidents: the 2010 discovery by the Defense Department that thousands of its computers were sending military network data to China due to code hidden in chips that handle the server startup process; Intel's discovery in 2014 that a Chinese hacking group penetrated its network via a server that fetched malware from an unidentified supplier's update site; and a 2015 warning issued by the FBI to multiple companies that Chinese agents had hidden an extra chip with backdoored code on one manufacturer's servers.
In other words, Bloomberg has expanded its claim that chips containing malicious spyware were added to Supermicro server motherboards, to also include claims of malicious alterations to BIOS-level software to load and run surveillance code hidden in firmware, and to include alleged attacks on other vendors.